Seit gestern ca. 23.30 sind Störungen im Freifunk-Netz.!
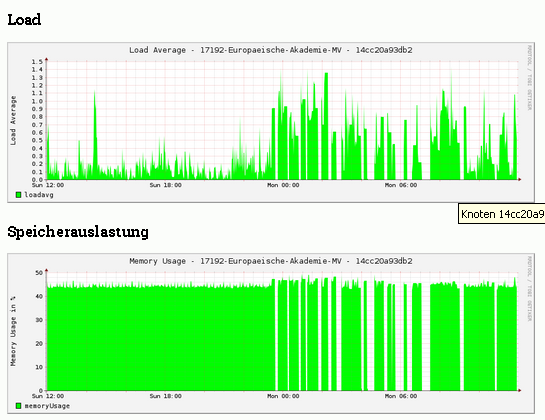
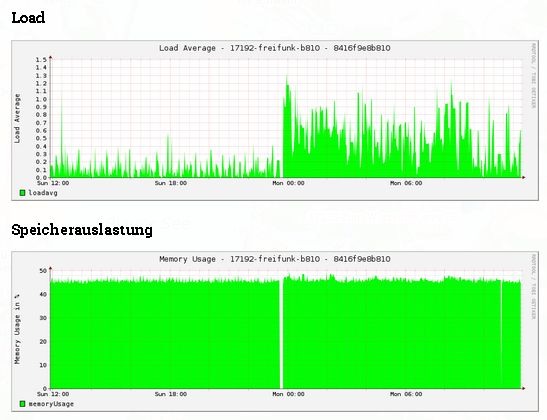
So ähnlich sieht es fast auf allen Knoten aus …
Hmm, ich sehe fehlende Daten und wohl einen Reboot. Welcher Art sind denn die Netzprobleme?
Eben diese fehlenden Daten, die warscheinlich auf Nichterreichbarkeit von „alfred“ deutet und zurzeit keine IPv6-Erreichbarkeit der Knoten von außen.
Und zurzeit Sterben immer mehr Knoten, werden wiederbelebt, sterben …
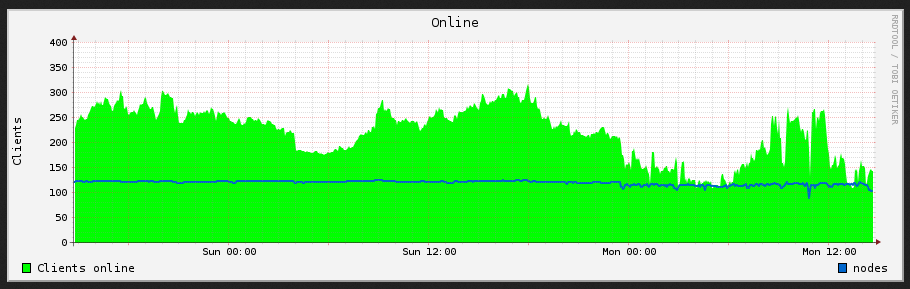
Andere Nutzer in der Region meinten, dass das Netz ist zurzeit extrem langsam ist.
Timeouts bei Ping mit Freifunk-WLAN auf map.4830.org könnten dies bestätigen.
C:\Windows\System32>ping map.4830.org
Ping wird ausgeführt für map.4830.org [192.251.226.106] mit 32 Bytes Daten:
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Antwort von 192.251.226.106: Bytes=32 Zeit=1019ms TTL=63
Antwort von 192.251.226.106: Bytes=32 Zeit=2161ms TTL=63
Ping-Statistik für 192.251.226.106:
Pakete: Gesendet = 4, Empfangen = 2, Verloren = 2
(50% Verlust),
Ca. Zeitangaben in Millisek.:
Minimum = 1019ms, Maximum = 2161ms, Mittelwert = 1590ms
C:\Windows\System32>ping -t map.4830.org
Ping wird ausgeführt für map.4830.org [2a06:e881:1700:1:5054:ff:feea:4f6] mit 32
Bytes Daten:
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=123ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=81ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=40ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=75ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=284ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=2356ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=227ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=55ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=251ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=553ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=369ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=72ms
Zeitüberschreitung der Anforderung.
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=1102ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=149ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=99ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=52ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=1209ms
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=66ms
Antwort von 2a06:e881:1700:1:5054:ff:feea:4f6: Zeit=84ms
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zielhost nicht erreichbar.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zielhost nicht erreichbar.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Zeitüberschreitung der Anforderung.
Ping-Statistik für 2a06:e881:1700:1:5054:ff:feea:4f6:
Pakete: Gesendet = 45, Empfangen = 19, Verloren = 26
(57% Verlust),
Ca. Zeitangaben in Millisek.:
Minimum = 40ms, Maximum = 2356ms, Mittelwert = 381msIch finde nix verdächtiges gw05 und die v6-Erreichbarkeit ist soweit auch gegeben?
root@de6:~# traceroute 2001:bf7:170::12fe:edff:fecd:b9d0
traceroute to 2001:bf7:170::12fe:edff:fecd:b9d0 (2001:bf7:170:0:12fe:edff:fecd:b9d0), 30 hops max, 80 byte packets
1 gateway (2a02:e00:ffec::1) 0.660 ms 0.696 ms 0.814 ms
2 strato.dus.ecix.net (2001:7f8:8::1a44:0:1) 16.476 ms 16.533 ms 16.445 ms
3 ae1.0.core-b30.as6724.net (2a01:238:0:30ad::1) 16.417 ms 16.415 ms 16.510 ms
4 bgp-ber01.4830.org (2a06:e881:1706:1::1) 15.267 ms 15.351 ms 15.234 ms
5 bgp-gut01.4830.org (2a06:e881:1700:1:400:c0ff:fefb:e277) 26.056 ms 25.980 ms 26.036 ms
6 gw05.4830.org (2a06:e881:1700:1::c0fb:e242) 26.339 ms 25.848 ms 25.747 ms
7 2001:bf7:170:0:12fe:edff:fecd:b9d0 (2001:bf7:170:0:12fe:edff:fecd:b9d0) 62.690 ms 62.745 ms 63.070 ms
Moin,
hmm, in der Tat, fastd ist am Anschlag; ist das Netz jüngst stärker gewachsen?
1391 root 20 0 112396 3032 1836 R 99.9 0.3 13067:21 fastd
99% CPU bei fastd heißt “alles Kacke für alle” 
Möchte ungerne noch eine VM mit fastd ausrollen, wobei gw06 steht ja latent bereit. Ich guck’ heute abend mal, das da fix geht.
auf 2 Knoten in Feldberg hatte ich seit gestern Abend diese Fehlermeldungen:
Mon Aug 6 14:28:16 2018 kern.warn kernel: [13669.903420] net_ratelimit: 2 callbacks suppressed
Mon Aug 6 14:28:16 2018 kern.warn kernel: [13669.908214] br-client: received packet on bat0 with own address as source address
Mon Aug 6 14:28:16 2018 kern.warn kernel: [13670.088587] br-client: received packet on bat0 with own address as source address
nachdem ich jetzt bei beiden Knoten gw06 & gw08 rausgenommen habe läuft es scheinbar wieder stabiler und ohne die »Loop« Fehler
uci set fastd.mesh_vpn_backbone_peer_gw06.enabled='0'
uci set fastd.mesh_vpn_backbone_peer_gw08.enabled='0'
gw06muer = { key = 'be56eb2cb9493f22b6e0cce4c7f8c838fd44e8c44c6983c58265bbe1c2cf04c0', remotes = {'ipv4 "gw06.4830.org" port 10169'}, }, gw06 = { key = 'be56eb2cb9493f22b6e0cce4c7f8c838fd44e8c44c6983c58265bbe1c2cf04c0', remotes = {'ipv4 "gw06.4830.org" port 10234'}, }, gw08 = { -- event01 key = '21630f3eec4c38808b93947a5ac2f5eae39538b47e9225513bd2b2fa27c4593a', remotes = {'ipv4 "gw06.4830.org" port 10234'}, }
(beides Router mit der 1.0.0~76, Domain: fsl)
Lief doch nur ein paar Minuten nach dem fastd restart gut. Mittlerweile wieder extrem langsam.
liegt es evtl. da dran?
root@17258-Bahnhofstr-39-UAP:~# batctl td mesh-vpn`
17:57:34.473420 BAT de:ad:be:ef:00:00: BCAST, orig 62:b5:21:8f:eb:c3, seq 8236085, Warning - packet contains unknown ether type: 0x86dd
17:57:34.474676 BAT de:ad:be:ef:00:00: BCAST, orig 0a:84:25:2e:2d:4b, seq 9810795, Warning - packet contains unknown ether type: 0x86dd
17:57:34.475865 BAT de:ad:be:ef:00:00: BCAST, orig 0a:84:25:2e:2d:4b, seq 9810800, Warning - packet contains unknown ether type: 0x86dd
17:57:34.477249 BAT de:ad:be:ef:00:00: BCAST, orig 62:b5:21:8f:eb:c3, seq 8236078, Warning - packet contains unknown ether type: 0x86dd
17:57:34.477617 BAT de:ad:be:ef:00:00: BCAST, orig 62:b5:21:8f:eb:c3, seq 8236079, Warning - packet contains unknown ether type: 0x86dd
17:57:34.481133 BAT de:ad:be:ef:00:00: BCAST, orig 62:b5:21:8f:eb:c3, seq 8236081, Warning - packet contains unknown ether type: 0x86dd
17:57:34.482115 BAT de:ad:be:ef:00:00: BCAST, orig 0a:84:25:2e:2d:4b, seq 9810801, Warning - packet contains unknown ether type: 0x86dd
17:57:34.482984 BAT de:ad:be:ef:00:00: BCAST, orig 62:b5:21:8f:eb:c3, seq 8236082, Warning - packet contains unknown ether type: 0x86dd
17:57:34.487213 BAT de:ad:be:ef:00:00: BCAST, orig 62:b5:21:8f:eb:c3, seq 8236083, Warning - packet contains unknown ether type: 0x86dd
17:57:34.487578 BAT de:ad:be:ef:00:00: BCAST, orig 62:b5:21:8f:eb:c3, seq 8236084, Warning - packet contains unknown ether type: 0x86dd
17:57:34.488308 BAT de:ad:be:ef:00:00: BCAST, orig 62:b5:21:8f:eb:c3, seq 8236086, Warning - packet contains unknown ether type: 0x86dd
17:57:34.489643 BAT de:ad:be:ef:00:00: BCAST, orig 62:b5:21:8f:eb:c3, seq 8236087, Warning - packet contains unknown ether type: 0x86dd
17:57:34.491450 BAT de:ad:be:ef:00:00: BCAST, orig 0a:84:25:2e:2d:4b, seq 9810797, Warning - packet contains unknown ether type: 0x86dd
17:57:34.493286 BAT de:ad:be:ef:00:00: BCAST, orig 62:b5:21:8f:eb:c3, seq 8236094, Warning - packet contains unknown ether type: 0x86dd
17:57:34.494044 BAT de:ad:be:ef:00:00: BCAST, orig 0a:84:25:2e:2d:4b, seq 9810802, Warning - packet contains unknown ether type: 0x86dd
17:57:34.497782 BAT de:ad:be:ef:00:00: BCAST, orig 62:b5:21:8f:eb:c3, seq 8236091, Warning - packet contains unknown ether type: 0x86dd’
Hallo Kai,
ich vermute, dass das auch nicht so sein soll:
Mon Aug 6 19:50:17 2018 kern.warn kernel: [ 1019.764385] net_ratelimit: 48 callbacks suppressed
Mon Aug 6 19:50:17 2018 kern.warn kernel: [ 1019.769313] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:17 2018 kern.warn kernel: [ 1019.863140] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:17 2018 kern.warn kernel: [ 1019.955358] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:17 2018 kern.warn kernel: [ 1020.033005] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:17 2018 kern.warn kernel: [ 1020.127865] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:17 2018 kern.warn kernel: [ 1020.177242] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:17 2018 kern.warn kernel: [ 1020.187013] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:17 2018 kern.warn kernel: [ 1020.230739] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:18 2018 kern.warn kernel: [ 1020.464512] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:18 2018 kern.warn kernel: [ 1020.538751] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:22 2018 kern.warn kernel: [ 1024.979953] net_ratelimit: 40 callbacks suppressed
Mon Aug 6 19:50:22 2018 kern.warn kernel: [ 1024.984831] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:22 2018 kern.warn kernel: [ 1025.178879] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:22 2018 kern.warn kernel: [ 1025.275333] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:23 2018 kern.warn kernel: [ 1025.510850] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:23 2018 kern.warn kernel: [ 1025.594840] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:23 2018 kern.warn kernel: [ 1025.651904] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:23 2018 kern.warn kernel: [ 1025.760663] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:23 2018 kern.warn kernel: [ 1025.891737] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:23 2018 kern.warn kernel: [ 1025.990566] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:23 2018 kern.warn kernel: [ 1026.244338] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:27 2018 kern.warn kernel: [ 1030.196970] net_ratelimit: 52 callbacks suppressed
Mon Aug 6 19:50:27 2018 kern.warn kernel: [ 1030.201858] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:27 2018 kern.warn kernel: [ 1030.246562] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:27 2018 kern.warn kernel: [ 1030.332107] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:27 2018 kern.warn kernel: [ 1030.363629] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:28 2018 kern.warn kernel: [ 1030.432151] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:28 2018 kern.warn kernel: [ 1030.509261] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:28 2018 kern.warn kernel: [ 1030.542296] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:28 2018 kern.warn kernel: [ 1030.619146] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:28 2018 kern.warn kernel: [ 1030.740929] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:28 2018 authpriv.info dropbear[5216]: Child connection from fd39:e4e3:eee1::a5e9:2e70:b65a:2181:1500
Mon Aug 6 19:50:28 2018 kern.warn kernel: [ 1030.836389] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:32 2018 kern.warn kernel: [ 1035.272955] net_ratelimit: 56 callbacks suppressed
Mon Aug 6 19:50:32 2018 kern.warn kernel: [ 1035.277890] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:32 2018 kern.warn kernel: [ 1035.317947] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:33 2018 kern.warn kernel: [ 1035.410670] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:33 2018 kern.warn kernel: [ 1035.459357] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:33 2018 kern.warn kernel: [ 1035.554835] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:33 2018 kern.warn kernel: [ 1035.591949] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:33 2018 kern.warn kernel: [ 1035.684557] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:33 2018 kern.warn kernel: [ 1035.728307] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:33 2018 kern.warn kernel: [ 1035.859357] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:33 2018 kern.warn kernel: [ 1035.954060] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:38 2018 kern.warn kernel: [ 1040.412279] net_ratelimit: 31 callbacks suppressed
Mon Aug 6 19:50:38 2018 kern.warn kernel: [ 1040.417193] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:38 2018 kern.warn kernel: [ 1040.593507] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:38 2018 kern.warn kernel: [ 1040.659048] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:38 2018 kern.warn kernel: [ 1040.755038] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:38 2018 kern.warn kernel: [ 1040.940024] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:38 2018 kern.warn kernel: [ 1041.023122] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:38 2018 kern.warn kernel: [ 1041.111438] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:38 2018 kern.warn kernel: [ 1041.305789] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:39 2018 kern.warn kernel: [ 1041.472407] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:39 2018 kern.warn kernel: [ 1041.657164] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:45 2018 kern.warn kernel: [ 1047.931890] net_ratelimit: 30 callbacks suppressed
Mon Aug 6 19:50:45 2018 kern.warn kernel: [ 1047.936812] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:45 2018 kern.info kernel: [ 1047.944504] IPv6: br-client: IPv6 duplicate address 2001:bf7:170:0:16cc:20ff:fecd:4e86 detected!
Mon Aug 6 19:50:45 2018 kern.warn kernel: [ 1048.071144] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:45 2018 kern.warn kernel: [ 1048.206181] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:46 2018 kern.warn kernel: [ 1048.430499] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:46 2018 kern.warn kernel: [ 1048.459179] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:46 2018 kern.warn kernel: [ 1048.550240] br-client: received packet on bat0 with own address as source address
Mon Aug 6 19:50:46 2018 kern.warn kernel: [ 1048.675436] br-client: received packet on bat0 with own address as source address
root@17194-Tressow-4e86:~#Besser? Habe gw05.4830.org rebootet …
Danke. Es hat sich leider nichts verbessert. 
Diese Meldungen habe ich auf den fünf Knoten ( 3x 1.0.0~76 und 2x 0.7.9~133), wo ich mich verbinden konnte.
Mon Aug 6 20:45:51 2018 kern.warn kernel: [ 1300.279713] br-client: received packet on bat0 with own address as source address
Mon Aug 6 20:45:52 2018 kern.warn kernel: [ 1300.516359] br-client: received packet on bat0 with own address as source address
Mon Aug 6 20:45:52 2018 kern.warn kernel: [ 1300.763450] br-client: received packet on bat0 with own address as source address
Mon Aug 6 20:45:52 2018 kern.warn kernel: [ 1301.197474] br-client: received packet on bat0 with own address as source addressIst zwar eine blöde Aussage, aber netzseitig wurde nichts verändert.
fastd ist nun nach Reboot bei 66-75% CPU, im Speedtest bekomme ich jeweils ca. 4 MBit/sec durch den 841er mit Müritzer Mesh. Am 03.08. waren’s noch 9/8, insofern kann ich bestätigen, daß sich was geändert hat, sehe aber nicht, was 
irgendwer irgendwo nen loop gebaut?
Hmm …
ffmuer@map:~$ ./find_mac.sh 62:b5:21:8f:eb:c3
62:b5:21:8f:eb:c3 at 201808062239 on 62:b5:21:8f:eb:c3 c4:e9:84:b0:a7:a8 "17192-Gemeindehaus-Kargow-a7a8" 53.506361 12.783583
ffmuer@map:~$ ./find_mac.sh 0a:84:25:2e:2d:4b
0a:84:25:2e:2d:4b at 201808062239 on 0a:84:25:2e:2d:4b 84:16:f9:d9:8f:9e "17194-Tressow-8f9e" 53.62695766 12.66972005
Das klingt nach Brückung (ich seh’ aber keine anderen GWs) oder zwei Clients per gelbem Port verbunden.
EDIT: Ich glaube, das Skript taucht nicht (oder ich raff’ die Ausgabe nicht):
ffmuer@map:~$ ./find_mac.sh 62:b5:21:8f:eb:c3
62:b5:21:8f:eb:c3 at 201808062251 on 62:b5:21:8f:eb:c3 18:d6:c7:51:9b:82 "17192-Martin-Router-King" 53.50892207 12.69160151 ("TP-Link TL-WR1043N/ND v4")

Ich hatte gestern meine CPEs nur 1:1 auf 1.0.0~73 gebracht bzw. bringen wollen. (siehe Firmware 1.0 ).
Diese sind nun wieder auf 0.7.9.0~133, weil ich dachte, die Firmware macht die derzeitigen Probleme. Später vermutete ich auch einen Loop, habe die “Stecker” gezogen und die CPEs nur per Mesh on IBSS und VPN erlaubt (zurzeit kein LAN/WAN).  Die Situation hat sich danach aber auch nicht gebessert.
Die Situation hat sich danach aber auch nicht gebessert.
“17194-Tressow-8f9e” hängt in der Garage - nur Strom.
“17192-Gemeindehaus-Kargow-a7a8” ist auf dem Dach des Gemeindezentrums und sollte über ‘Mesh-on-WAN’ mit “17192-Gemeindehaus-Kargow” (GELB ‘Mesh-on-LAN’) verbunden sein.
 Sonntag Abend ist dort i.d.R. keine Party, wo ‘Streiche’ gespielt werden könnten.
Sonntag Abend ist dort i.d.R. keine Party, wo ‘Streiche’ gespielt werden könnten.
Bei den CPEs war das vor v2016.1 in der Tat ein Problem, da stimmte irgendwie das MAC-Munging nicht. Aber das sollte längst gefixt sein (und mit dem Rückschritt auf 0.7 der Spuk vorbei) …
Hmm, geht vielleicht die Einstellung Mesh-on-LAN/WAN beim Upgrade flöten? Wild guess, paßte aber zum Symptom? Kannst Du gucken, ob MoL wirklich noch aktiv ist?
Beim Upgrade von 0.7.9 nach 1.x und zurück übernehme ich i.d.R. keine Konfiguration … alles wieder zu Fuß  und die Knoten in “17192-Gemeindehaus-Kargow” hatten keine Upgrades bekommen.
und die Knoten in “17192-Gemeindehaus-Kargow” hatten keine Upgrades bekommen.
Meine Knoten sind erstmal OFFLINE. Strom sparen.
Morgen früh, wenn der Hahn kräht und die Motorsense vom Nachbarn knattert, schalte ich die Knoten wieder an … falls es doch an denen liegen sollte